Imagine you wish to run a game engine locally on LAN and benefit from the features of a managed database in the cloud, where the game engine is separated from the game database holding quests, artifacts, loots offering persistency and automated backups. Or imagine an enterprise set-up where the front end UI is hosted on the company network but the expensive GPUs back-end machines are rented from a cloud provider. In this case, the jargon calls the set-up “hybrid cloud“, partially on-prem and partially on the cloud, but here is the deal: a connection between the two locations is necessary before anything else, and that is what this article is about.
Below is the general idea; there is the router on the left at home or your company datacenter, the IPsec connection in the middle plus DRG, itself attached to VCNs (virtual networks) on the cloud.
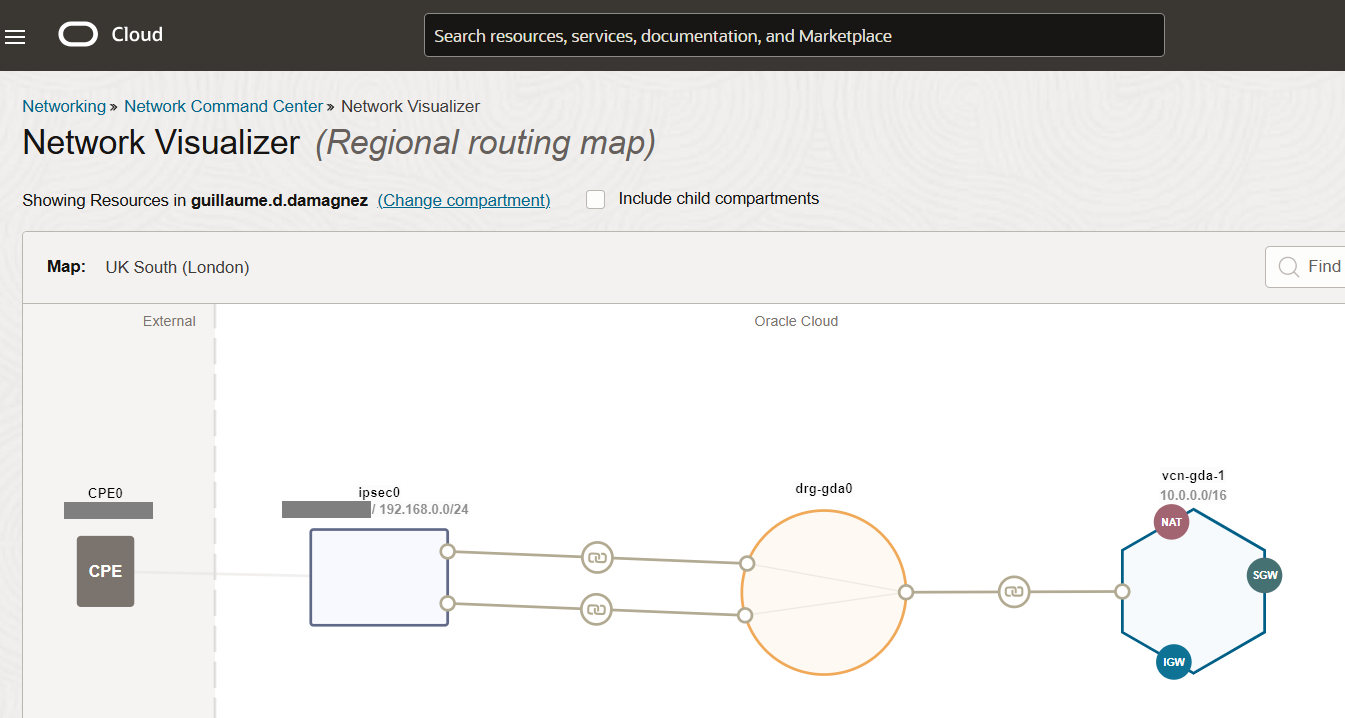
I am using an old Cisco 2921 as router and a TP Link TD-W9970 as modem for this home lab.

Now the set-up now shall we? Configure the TP Link TD-W9970 in bridge mode as you only want the device to pass the signal to the router.
On to the router now, it is a Cisco 2921 with iOs version 15.2. This does require a tiny bit of Cisco knowledge and is the most challenging part of the project😭. I am pretty sure there are more user friendly routers out there to do that but that is all I have 🤷
version 15.2
service timestamps debug datetime msec
service timestamps log datetime msec
no service password-encryption
!
hostname Router1
!
boot-start-marker
boot-end-marker
!
!
!
no aaa new-model
!
ip cef
!
!
!
ip dhcp excluded-address 192.168.0.1 192.168.0.10
!
ip dhcp pool MYPOOL
network 192.168.0.0 255.255.255.0
default-router 192.168.0.1
dns-server 8.8.8.8
!
!
!
ip domain name net.home
no ipv6 cef
!
multilink bundle-name authenticated
!
!
!
!
license udi pid CISCO2921/K9 sn FCZ175270LA
!
!
username admin privilege 15 secret 4 TVbX4iUhR7.oz76TRrxlSuKpT4fRahq6bfIqf4vznS.
!
redundancy
!
!
!
!
!
ip ssh version 2
!
crypto keyring oracle-vpn-A.A.A.A
local-address B.B.B.B
pre-shared-key address A.A.A.A key oHpcZI6PSVJz8EF6KOFXqJDmtzgLdYnVIavQNKHgTx5OwYTEtFBTjm0AEjBs0Jge
!
crypto isakmp policy 10
encr aes 256
hash sha384
authentication pre-share
group 5
lifetime 28800
crypto isakmp fragmentation
crypto isakmp keepalive 10 10
crypto isakmp profile oracle-vpn-A.A.A.A
keyring oracle-vpn-A.A.A.A
self-identity address
match identity address A.A.A.A 255.255.255.255
!
crypto ipsec security-association replay window-size 128
!
crypto ipsec transform-set oracle-vpn-transform esp-aes 256 esp-sha-hmac
mode tunnel
crypto ipsec df-bit clear
!
!
crypto ipsec profile oracle-vpn
set transform-set oracle-vpn-transform
set pfs group5
!
!
!
!
!
!
interface Tunnel1
ip address 172.16.1.1 255.255.255.252
tunnel source B.B.B.B
tunnel mode ipsec ipv4
tunnel destination A.A.A.A
tunnel protection ipsec profile oracle-vpn
!
interface Embedded-Service-Engine0/0
no ip address
shutdown
!
interface GigabitEthernet0/0
no ip address
ip access-group OCI in
duplex auto
speed auto
pppoe enable group global
pppoe-client dial-pool-number 1
!
interface GigabitEthernet0/1
ip address 192.168.0.1 255.255.255.0
ip nat inside
ip virtual-reassembly in
ip tcp adjust-mss 1452
duplex auto
speed auto
!
interface GigabitEthernet0/2
no ip address
shutdown
duplex auto
speed auto
!
interface Dialer1
mtu 1492
ip address negotiated
ip nat outside
ip virtual-reassembly in
encapsulation ppp
dialer pool 1
dialer-group 1
ppp chap hostname johndoe.btclick.com
ppp chap password 0 Welcome1
ppp pap sent-username johndoe.btclick.com password 0 Welcome1
!
ip forward-protocol nd
!
no ip http server
no ip http secure-server
!
ip nat inside source list 1 interface Dialer1 overload
ip route 0.0.0.0 0.0.0.0 Dialer1
ip route 10.0.0.0 255.255.0.0 Tunnel1
!
ip access-list extended OCI
permit udp host A.A.A.A host B.B.B.B eq isakmp
permit esp host A.A.A.A host B.B.B.B
permit icmp any any echo
permit icmp any any echo-reply
permit icmp any any unreachable
!
access-list 1 permit 192.168.0.0 0.0.0.255
!
!
!
control-plane
!
!
!
line con 0
line aux 0
line 2
no activation-character
no exec
transport preferred none
transport output pad telnet rlogin lapb-ta mop udptn v120 ssh
stopbits 1
line vty 0 4
login local
transport input ssh
!
scheduler allocate 20000 1000
!
end- The beginning is about my local DHCP server and how IP addresses are allocated, please ignore.
- A.A.A.A would be the address of the Oracle end-point, how to enters into OCI, it is available on the console on the tunnel view.
- B.B.B.B is your on-prem router IP address, also called customer CPE.
- Then the Crypto commands, I am unfamiliar with these but here is the general idea; you need to make both endpoints trust each other and exchange key, exchange a few details about how they are going to communicate and setup a “transform set” to allow for the cypher to kick off.
- Then you’ve got your tunnel itself which is considered an interface where you give source and destination as well as the “tunnel inside IP address”; you’ll need it for debugging and to make sense of the traceroute command later.
- G0/0 is my interface connected with the TP-Link modem and its PPPoE set-up facing the internet (facing my ISP)
- G0/1 is my LAN interface, do not forget the tcp adjust-mss 1452 which gave me a lot of grief; I could access the internet and ping, but it was dead slow on showing pages and would not show anything if I’d be accessing big pages like login pages.
- Dialer 1 is the interface handling the login with the ISP and other details; do not forget to set MTU as 1492. The MTU and MSS are related to packet sizes and headers inside these, without it the Router does not know how to “cut” packets.
- You’ve got two routes saying which traffic goes where, so it starts with the most specific at 10.0.0.0/16 will be sent via the tunnel and any left over goes out to the internet via Dialer1.
- Some security lists to allow the protocol exchange between the VPN endpoints on the Oracle side and the CPE side. I am not too confident with this so can’t comment much.
- The end is related to SSH access to the router, ignore this part.
This is mostly copy paste from Oracle Documentation here, plus some adaptations to my LAN; Note this code will only set-up 1 tunnel here, just because I don’t want to make the setup even more bloated.
Let’s go on the Oracle OCI console now
- Create a VCN.
- Create a DRG, Dynamic Routing Gateway, and attach the VCN to it from the DRG main view. A DRG is a virtual router.
- Create a CPE and enter your router IP address.
- Create an IP Sec connection “Site-to-site” and attach it to the DRG during its creation process, select your CPE and enter the route to you on-prem, in my case 192.168.x.x/24, select IKEv1, static routing and only set-up a single tunnel. Enter IPs for both ends inside the tunnel like so IPv4 inside tunnel interface – CPE and IPv4 inside tunnel interface – Oracle e.g. 172.16.0.1/30 and 172.16.0.2/30 that’s what I use.
- Go to the Oracle OCI subnet supposed to talk to your on-prem system and lift security list restrictions on traffic coming from 192.168.x.x/24, also modify the route table there and add a route rule to point traffic 192.168.x.x/24 via DRG.
- Verify the DRG route tables, go back to your DRG and select the routes; open them and click “get all route rules”. Make sure you find both routes going On-prem -> OCI pointing to vcn and OCI -> On-prem pointing to drg.
Wow, let’s hope we’ve got some green lights on the tunnels now or at least some meaningful errors messages 🤞
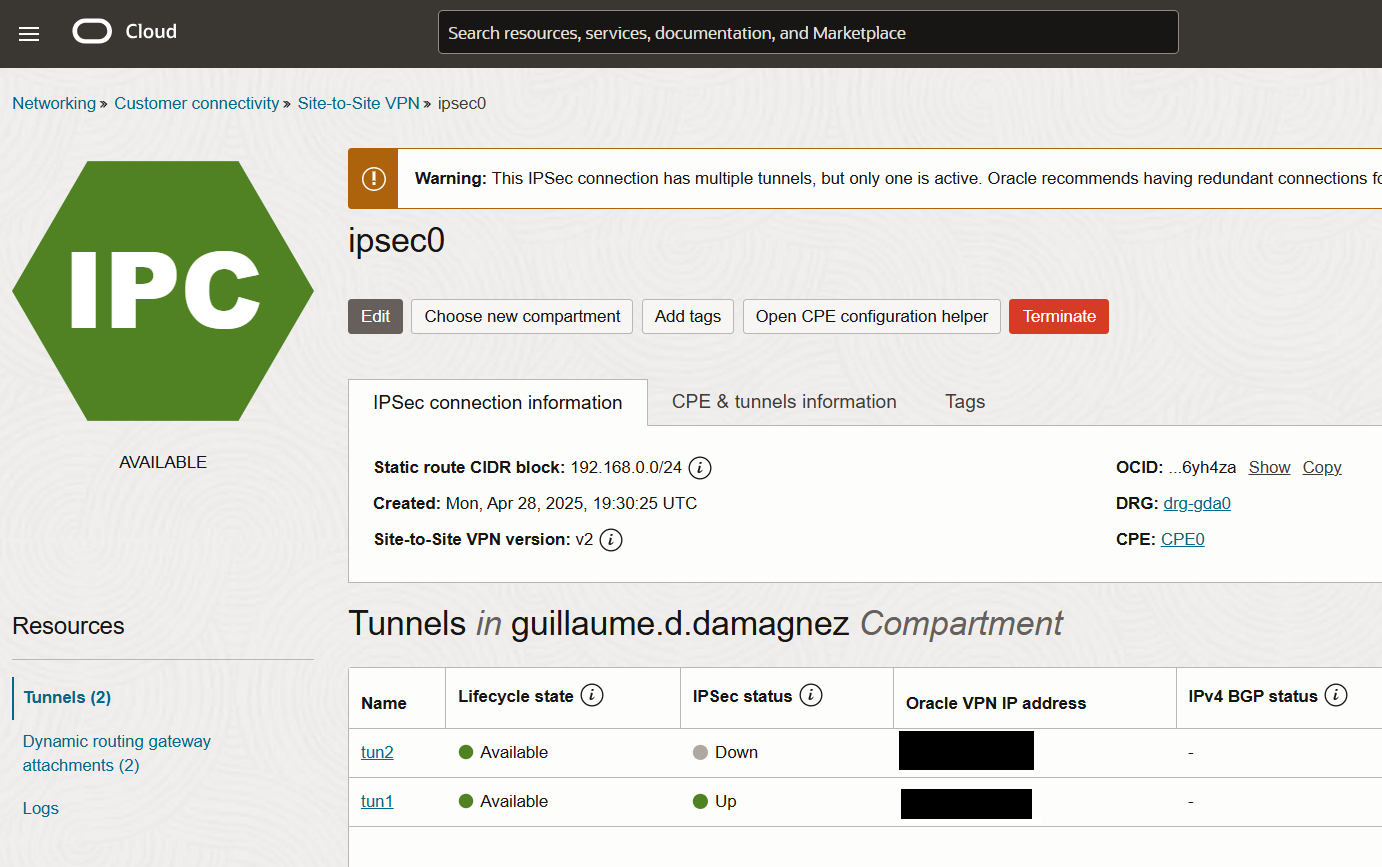
Tunnel 1 looks promising! You can crack a can of beer I approve it. 🏆
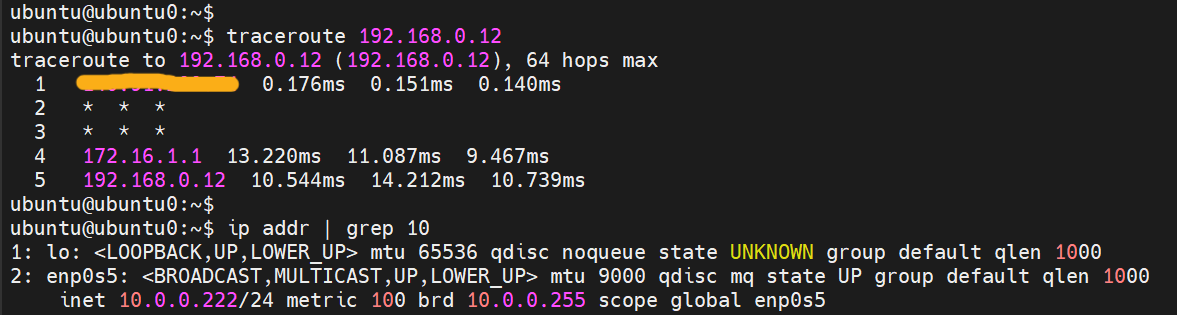
If you’ve succeeded with these steps you can launch the firsts pings and traceroutes. Below is an ubuntu0 machine in Oracle OCI at 10.0.0.222 on 10.0.0.0/16 vcn. It goes via a first router belonging to Oracle, most likely the DRG, then enters the tunnel, hits the other side of the tunnel at my router at home (or CPE side), enters my LAN and goes to the end destination at 192.168.0.12 which is my Kali machine.
Same on my Kali now to the cloud. Hits my router locally, enters the tunnel, hits the DRG, get sent to the VCN and finds ubuntu0 at 10.0.0.222.
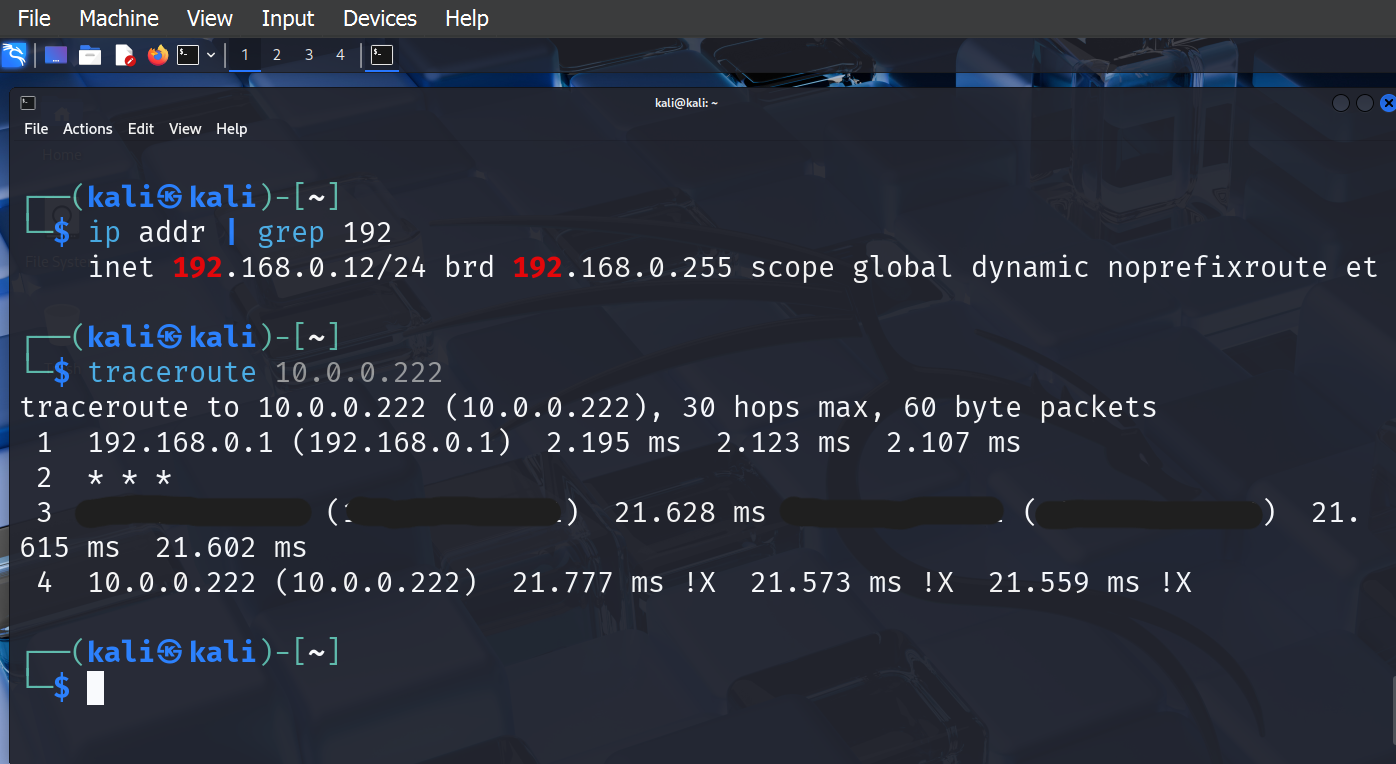
Same test of reachability test below from Kali but using another protocol
That’s it, you have got yourself an hybrid set-up now on which you can build the lab of your dreams :D.
Two ways to make it better I can think of, set up the other tunnel tun2 as the console recommends and to enable BGP, which will be a must in a corporate environment! Open to any correction, comment or suggestion 🙂
*BGP is a way to advertise networks e.g. if you look at my Cisco router on the first picture I have a port at g0/2 available, I could plug a cable there and decide to have another network e.g. 172.18.3.0/24; then this network would be automatically passed to OCI, it would build the routes automatically for us and my ubuntu0 machine would be able to ping machines on this newly formed local network without further set-up.